Software Security Labs 
-

New: Shellcode Development Lab

Shellcode is widely used in code injection attacks, and writing shellcode is challenging. In this lab, students will write shellcode from scratch, so they can learn the underlying techniques.
-

Buffer Overflow Vulnerability Lab

Launching attack to exploit the buffer-overflow vulnerability using shellcode. Conducting experiments with several countermeasures.
-
Return-to-Libc Attack Lab

Using the return-to-libc technique to defeat the "non-executable stack" countermeasure of the buffer-overflow attack.
-
Environment Variable and Set-UID Lab

Launching attacks on privileged Set-UID root program. Risks of environment variables. Side effects of system().
-

Race Condition Vulnerability Lab

Exploiting the race condition vulnerability in privileged program. Conducting experiments with various countermeasures.
-

Dirty COW Attack Lab

Exploiting the Dirty COW race condition vulnerability in Linux kernel to gain the root privilege.
-

Format String Vulnerability Lab

Exploiting the format string vulnerability to crash a program, steal sensitive information, or modify critical data.
-
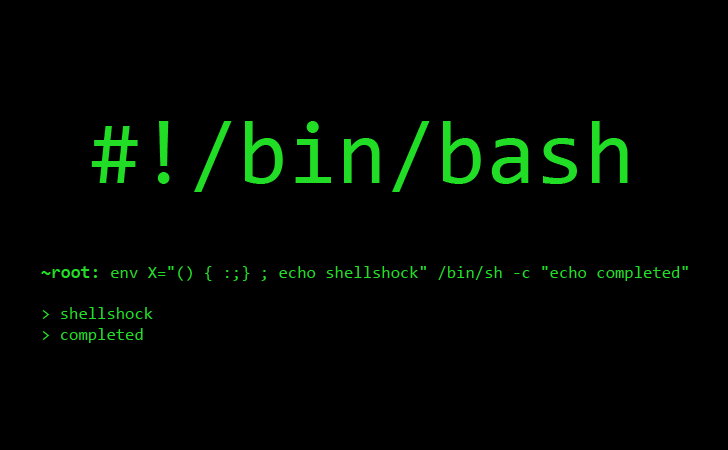
Shellshock Vulnerability Lab

Launch attack to exploit the Shellshock vulnerability that is discovered in late 2014.
