Environment Variable and Set-UID Lab
SEED Lab: A Hands-on Lab for Security Education
Overview
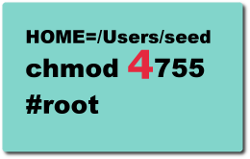
Set-UID is an important security mechanism in Unix operating systems. When a Set-UID program runs, it assumes the owner's privileges. For example, if the program's owner is root, then when anyone runs this program, the program gains the root's privileges during its execution. Set-UID allows us to do many interesting things, but unfortunately, it is also the culprit of many bad things. The objective of this lab is for students to understand what risks such privileged programs face and how they can be attacked if there are mistakes in the code.
Lab Tasks
- VM version: This lab has been tested on our pre-built SEEDUbuntu16.04 VM.
Recommended Time
- Supervised situation (e.g. a closely-guided lab session):
- Unsupervised situation (e.g. take-home project):
Videos (New)
- This topic is covered in my Udemy course: Computer Security: A Hands-on Approach.
Suggested Reading
- SEED Book by Wenliang Du
(Book website)
(Chinese version)
- Checklist for Security of Setuid Programs
- Chen, Wagner, and Dean. Setuid Demystified
- Bishop. How to write a Set-UID program